In a previous post, I explained why and how you could enforce the usage of product subscriptions within Azure API Management. As I was not entirely happy about the solution, I invested a little more time to check if Azure Policy could achieve the same result! And the answer is… YES! You can read how this can be done in this blog post!
Explore Azure Policy aliases
When using Azure Policy, you have to check that the properties of the resource type that you want to validate are available as an Azure Policy alias. This is how we can do this.
- Open PowerShell as Administrator
- Install the Az.Resources module and confirm
Install-Module Az.Resources
- Log in through this command and follow the instructions
Connect-AzAccount
- Check if there exist any Azure Policy aliases for Azure API Management subscriptions
(Get-AzPolicyAlias -NamespaceMatch 'Microsoft.ApiManagement' -ResourceTypeMatch 'service/subscriptions' -ListAvailable).Aliases
- The scope alias is interesting for our use case

Create policy definition
Now it is time to develop a policy definition that enforces the use of product subscriptions.
- Let’s create a new policy definition

- Provide some basic information

- Create the policy definition and click Save. This definition denies all API Management subscriptions that do not contain “/products/” in their scope.
{
"mode": "All",
"policyRule": {
"if": {
"allOf": [
{
"field": "type",
"equals": "Microsoft.ApiManagement/service/subscriptions"
},
{
"field": "Microsoft.ApiManagement/service/subscriptions/scope",
"notcontains": "/products/"
}
]
},
"then": {
"effect": "deny"
}
},
"parameters": {}
}
Create policy assignment
In order to activate the policy, we need to assign it to a specific scope.
- Click Assign
- Provide the scope to which you want to apply the policy. In my case, it is on resource group level. Click Create.

Test the policy
Let’s see if we can block the creation of an API subscription
- Navigate to an API Management instance that is located within the policy assignment scope.
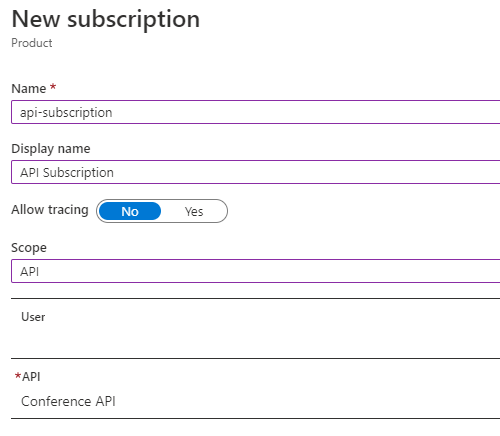
- Create a new subscription that is scoped to a single API
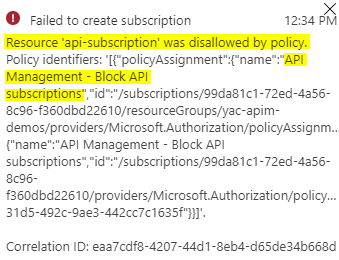
- When clicking on Save, you should see that the policy denied the creation of this subscription
Conclusion
Azure Policy is very powerful when it comes to modern cloud governance. Give freedom to your people, within strict boundaries. This is a very application-specific example of how Azure Policy can enforce product subscriptions. I prefer this approach compared to my previous blog, as you don’t have to think about it anymore as an API publisher – once it is configured.
Cheers,
Toon












