As the Microsoft Graph API is becoming more popular, I often get the question on how to authenticate Logic Apps against the Microsoft Graph API. When you search on the web, it looks like the only way to achieve this is by creating an App Registration and using the appropriate client id and secret to authenticate. However, this is not optimal for two reasons:
- The client secret needs to be shared
- The client secret will expire one day
To overcome these limitations, we must use Managed Identity. Unfortunately, the way to perform role assignments on Managed Identities is only available through scripting. This blog should help you out!
Configure the Logic App
Perform the following steps to configure the Logic App to use Managed Identity for consuming the Microsoft Graph API.
- First of all, let’s enable System-Assigned Managed Identity on our Logic App.
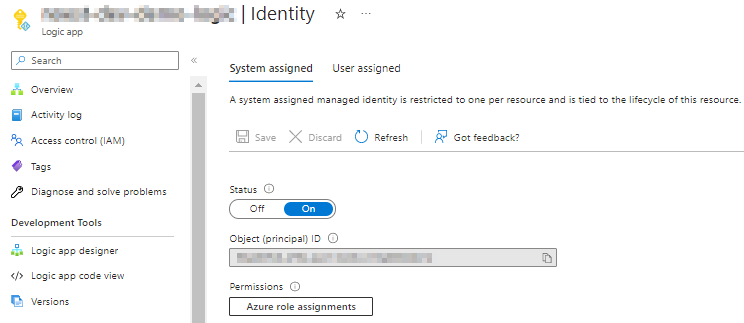
- As a second step, we need to configure the HTTP action to authenticate against Microsoft Graph, using that identity
- Authentication type: Managed Identity
- Managed identity: System-assigned managed identity
- Audience: https://graph.microsoft.com

Grant access to the Logic App
Now, we need to explicitly grant permissions to our Logic App’s Managed Identity. This can be done through the following PowerShell script and with elevated Azure AD permissions:
#Configure variables
$logicAppName="xxx"
$graphRole="User.Read.All"
#Query Azure AD
$spId=$(az resource list -n $logicAppName --query [*].identity.principalId --out tsv)
$graphResourceId=$(az ad sp list --display-name "Microsoft Graph" --query [0].id --out tsv)
$appRoleId=$(az ad sp list --display-name "Microsoft Graph" --query "[0].appRoles[?value=='$graphRole' && contains(allowedMemberTypes, 'Application')].id" --output tsv)
#Perform role assignments
$uri="https://graph.microsoft.com/v1.0/servicePrincipals/$spId/appRoleAssignments"
$body="{'principalId':'$spId','resourceId':'$graphResourceId','appRoleId':'$appRoleId'}"
az rest --method post --uri $uri --body $body --headers "Content-Type=application/json"
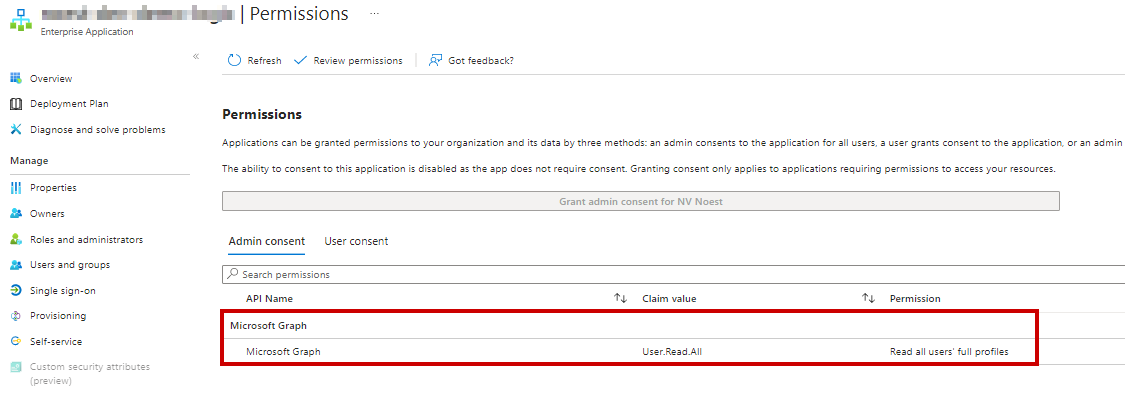
As a result, you can see that the User.Read.All application permission has been granted to our Managed Identity (which is an Enterprise Application).
Conclusion
A much better solution: no secrets to share and no secrets that might expire. Unfortunately, Azure AD still does not contain easy authoring of role assignments for Managed Identities. A real pity.
Sharing is caring!
Toon












