Security is one of my main concerns when building PaaS solutions in Azure. Since private endpoints have GA’d, I always apply network security on my projects. Unfortunately, private endpoints for Service Bus are only available in the Premium tier, which is a huge price difference. Because this extra cost is often not justifiable, I use Azure AD authentication to connect to Service Bus, which makes it more secure than SAS tokens. Certainly when you leverage managed identity, which allows secure connectivity without the need for passwords or SAS tokens.
Disable local authentication
New feature
Recently, a new feature has been introduced that disables the use of SAS tokens. You can find it on the home page of the Service Bus Namespace:
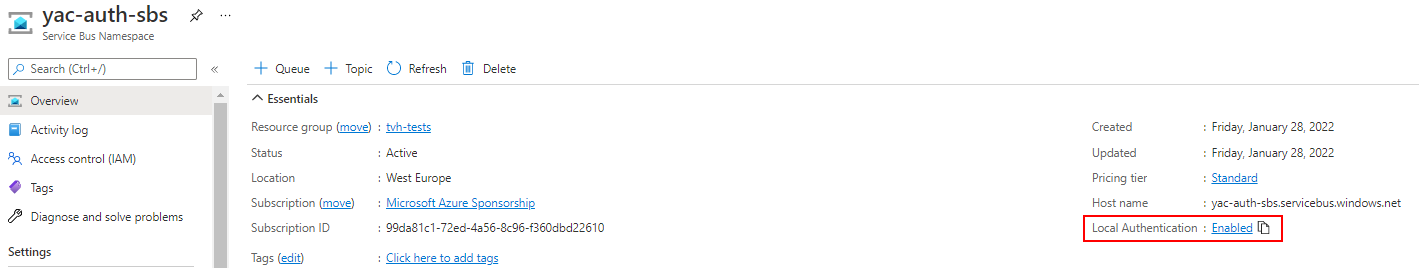
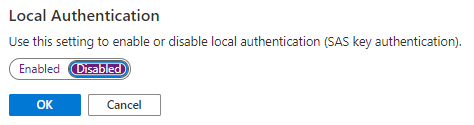
Choose to disable local authentication:
Bicep
If you want to disable this authentication via Bicep, you can set this via a simple boolean:
resource serviceBus 'Microsoft.ServiceBus/namespaces@2021-06-01-preview' = {
name: 'yac-auth-sbs'
location: resourceGroup().location
sku: {
name: 'Standard'
tier: 'Standard'
}
properties: {
disableLocalAuth: true
}
}
Shared Access Policies
I was curious if I am still able to create Shared Access Policies. This is still possible, but there is a nice warning that indicates that this functionality is currently disabled.

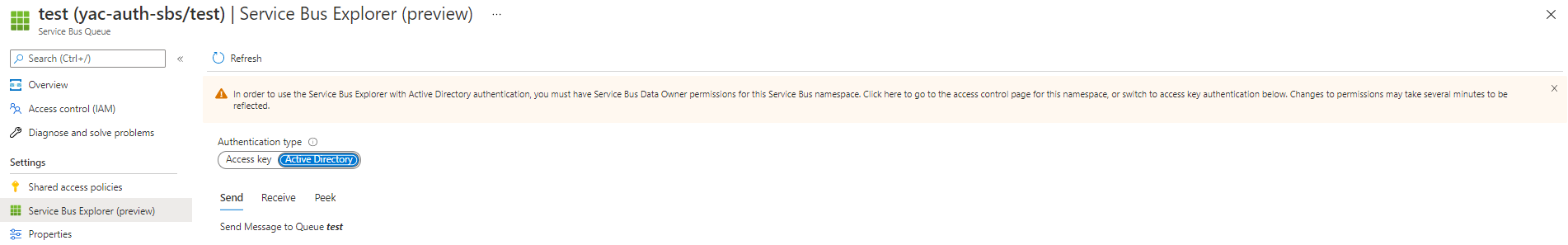
Service Bus Explorer
Service Bus Explorer typically works with SAS tokens. The product team did a great job and provides an option to choose between Access keys and Active Directory authentication. When you choose Azure AD, you must have sufficient rights on the data plane, by having the Service Bus Data Owner role.
Azure Policy
You can give the advice to disable local authentication to your team, but we’re all human and often forget such small settings. Luckily there is an Azure Policy available that allows you to enforce this: Azure Service Bus namespaces should have local authentication methods disabled. Disabling local authentication methods improves security by ensuring that Azure Service Bus namespaces exclusively require Azure Active Directory identities for authentication.
Event Hubs
It is good to know that Event Hubs also offers this functionality. More information can be found here.
Conclusion
Security-first is a good mindset! Great to see that more and more Azure Services have the option to enforce Azure AD authentication.
Happy learning!
Toon