Modern API security protocols, like OAuth2 and Open ID Connect, assume that all HTTP traffic is encrypted on the wire, using TLS. Therefor, it is a good security practice to enforce the usage of HTTPS within API Management. In Azure, the Azure Policy engine is designed to take up this responsibility. Let me show you how.
Explore Azure Policy aliases
When using Azure Policy, you have to check that the properties of the resource type that you want to validate are available as an Azure Policy alias. This is how we can do this.
- Open PowerShell as Administrator
- Install the Az.Resources module and confirm
Install-Module Az.Resources
- Log in through this command and follow the instructions
Connect-AzAccount
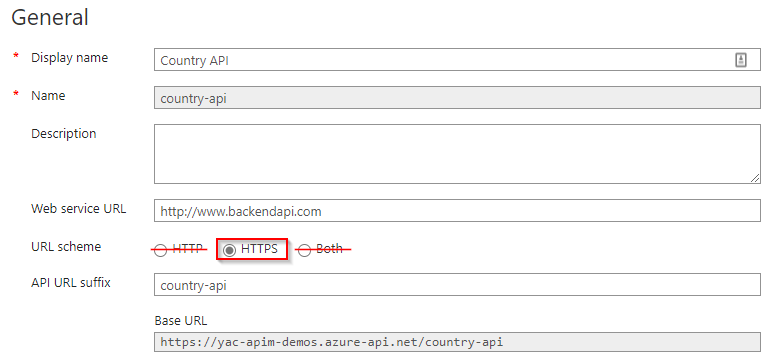
- Check if there exist any Azure Policy aliases for Azure API Management subscriptions
(Get-AzPolicyAlias -NamespaceMatch 'Microsoft.ApiManagement' -ResourceTypeMatch 'service/apis' -ListAvailable).Aliases
- The protocols[*] alias is the one we need to work with
Create policy definition
Now it is time to develop a policy definition that enforces HTTPS for each API.
- Let’s create a new policy definition

- Provide some basic information
- Create the policy definition and click Save. This definition denies every API that contains “http” within its allowed protocols. After some failed attempts, the documentation about the Count condition, explained me how I can verify that the protocols array contains the “http” value.
{
Create policy assignment
In order to activate the policy, we need to assign it to a specific scope.
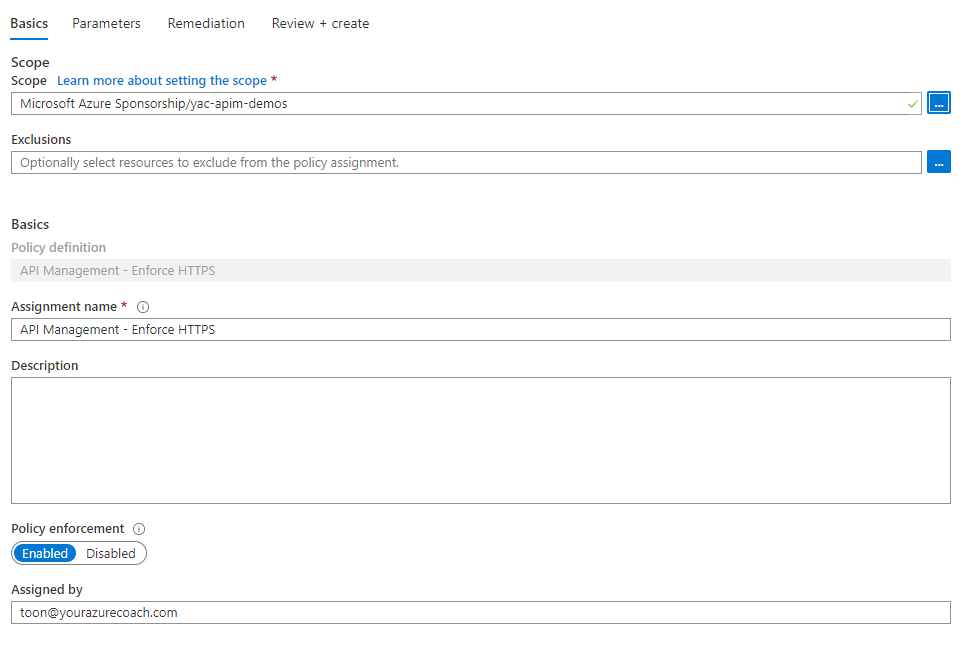
- Click Assign
- Provide the scope to which you want to apply the policy. In my case, it is on resource group level. Click Create.
Test the policy
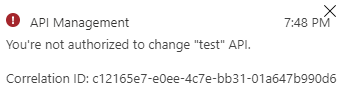
Navigate to one of the existing APIs and change the URL scheme to “HTTP” or “Both”. This operation should fail.
[Remark] At the time of writing, the exception that is shown indicates an unauthorized exception, instead of a policy enforcement message. This is not the desired error handling. This issue is passed to the product team and they will improve the error handling. I will update this post, when this is fixed.
Conclusion
Azure Policy is the best way to enforce compliance at scale. Although the development and testing experience is really cumbersome, the final result is very powerful.
Thanks for reading! And remember: sharing is caring!
Toon












