Since recently, Logic Apps has the ability to configure OAuth2 authorization on the HTTP trigger. You can define authorization policies, that perform basic validations on the claims inside the incoming Bearer token.

Role-based access control
When securing API endpoints, I tend to use Azure Active Directory Application Roles by default. It externalizes the access control from the applications where the authorization rules are enforced. If you are new to Azure AD application roles, you can find more about them here. When implementing role-based access control, you typically must validate the incoming bearer token on three things:
- Is the issuer valid?
- Is the audience valid?
- Does the consumer have the required role?
Within Logic Apps, the third validation rules cannot be configured with the standard Authorization policies. We need to check if the roles claim, which is an array, contains the required value.
RBAC in Logic Apps
As a workaround, we can perform this validation inside the Logic App itself. To achieve this, I use a *decision action* to determine whether the required role is included in the incoming bearer token.
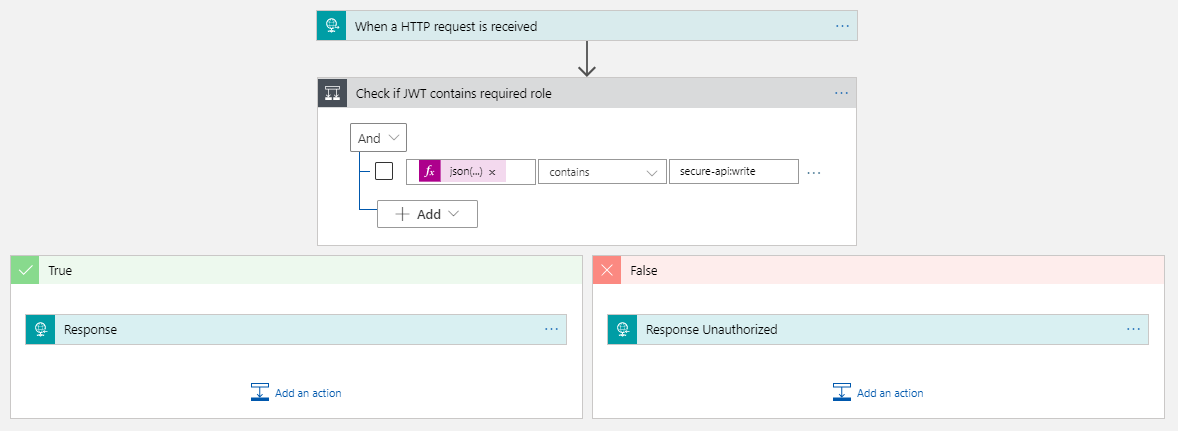
The first challenge is the fact that Logic Apps removes the Authorization header from the incoming request. You can by-pass this default behavior, by adding this operationOption to the Request trigger:
"request": {
"inputs": {
"schema": {}
},
"kind": "Http",
"type": "Request",
"operationOptions": "IncludeAuthorizationHeadersInOutputs"
}
The second challenge is figuring out how to interpret the roles claim inside the Authorization header, using the available Logic Apps expressions. I was able to do it like this:
contains(json(base64ToString(split(replace(triggerOutputs().headers.Authorization, 'Bearer ',''), '.')[1])).roles, 'secure-api:write')
Conclusion
Quite some workarounds to get role-based access control working. Would be great that the Authorization policies support the contains operator on custom claims.
Thanks for reading!
Toon












