Security must be key for every cloud solution. Azure Policy is one of your biggest companions to ensure that you enforce certain security policies. You can configure them in audit, deny or modify mode. However, it often takes a while to see the results once you’ve activated a policy, because these audit policies run asynchronously in the background. In some cases, you have the need to interactively query your Azure environment to discover potential security issues. For such cases, Azure Resource Graph – one of Azure’s unsung heroes – can be very usefull!
Scenario
In my case, I wanted to check if an Azure environment contained Azure App Services that both have:
- VNET integration enabled: which allows them to connect to private resources within their virtual network
- Public network access enabled: which makes them accessible on public internet
Azure App Service with such a configuration are a potential security risk.
Solution
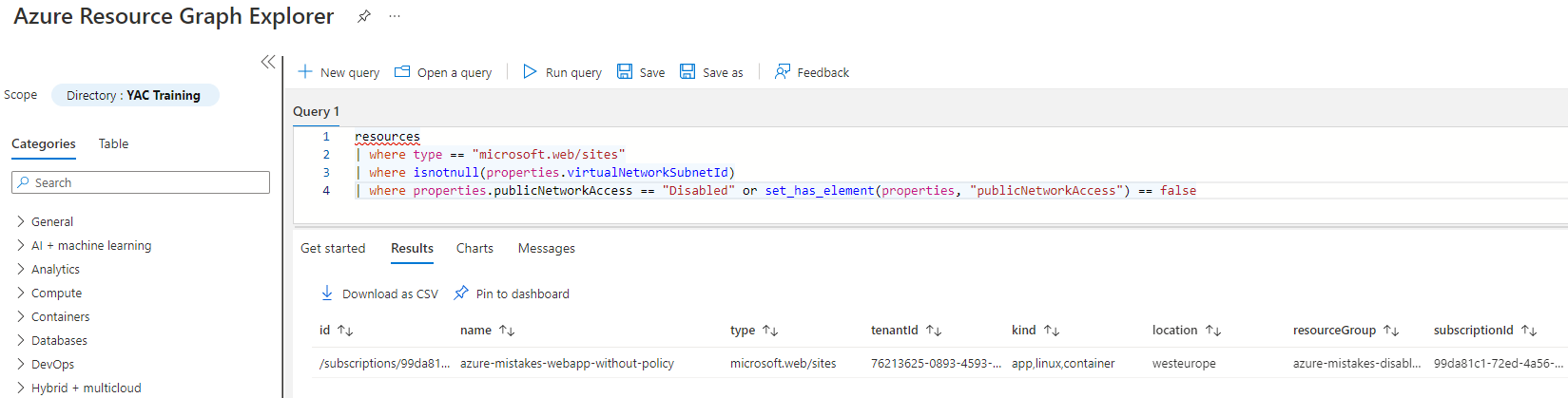
This is how you can easily identify these App Services:
- Open the Resource Graph Explorer via the Search bar at the top of the Azure Portal
- Paste the following query into the query pane
resources | where type == "microsoft.web/sites" | where isnotnull(properties.virtualNetworkSubnetId) | where properties.publicNetworkAccess == "Enabled" or set_has_element(properties, "publicNetworkAccess") == false
- Click on Run query and you can enjoy the result 🙂
Conclusion
Azure Resource Graph allows you to query your Azure environment rapidly by using the KQL language. You can use it to validate resource consistency, check monitoring settings, understand which Azure services that are being used… and it helps you to identity potential security risks. The biggest difference with Azure Policy is that it queries everything in an interactive way, which provides immediate results.












